- Audit of the ticketing system
Government, Central Region
Date
June 2024
Client
Govt, Central Region
Category
Cybersecurity
Location
Riyadh KSA
Customer is a service provider & has countrywide operation.
Project:
TeleNoc was assigned to conduct VAPT for the environment below & report vulnerabilities:
1. APIs
- 6 models of APIs, each with 20 operations.
2. Mobile Applications:
- Two mobile applications (Android and iOS).
3. Website and Web Application:
- A website with an integrated web application.
4. Back-Office Applications:
- Applications on SharePoint.
Solution:
A Vulnerability Assessment and Penetration Testing (VAPT) exercise was conducted to evaluate the security posture of the target systems, applications, and network infrastructure. The primary objective of this assessment was to identify potential security vulnerabilities, assess their impact, and determine the extent to which they could be exploited by an attacker. The vulnerability assessment phase involved systematic scanning and analysis to identify known weaknesses, misconfigurations, outdated software components, and security gaps. This was followed by the penetration testing phase, where selected vulnerabilities were actively exploited in a controlled and authorized manner to validate their severity and real-world exploitability.
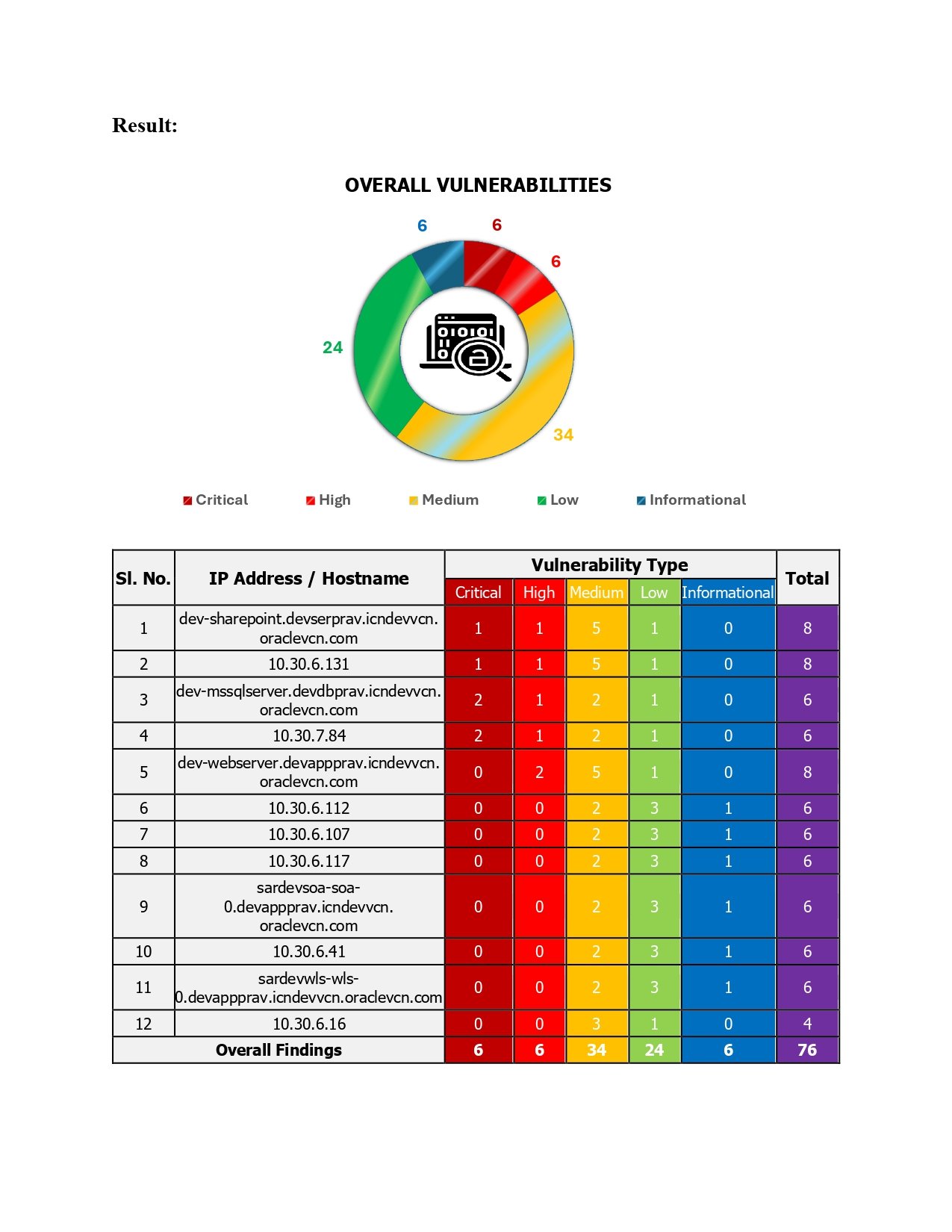
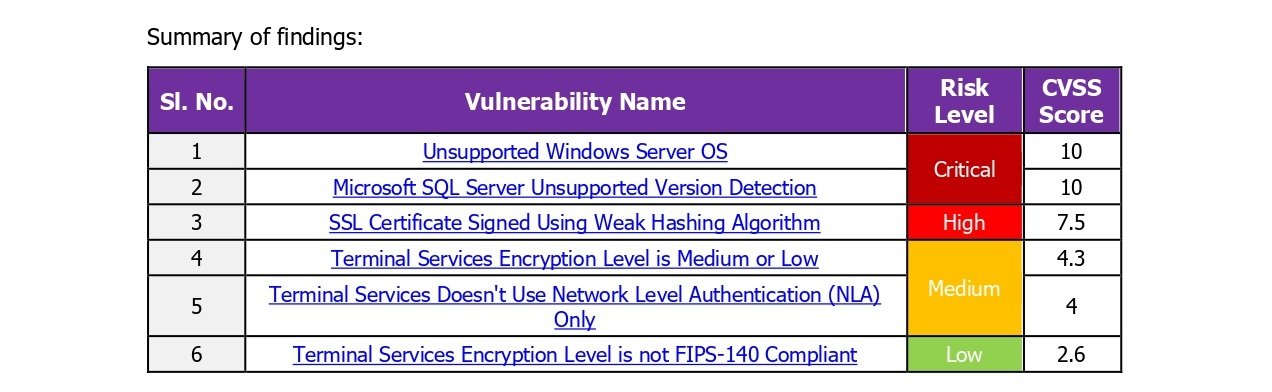
The assessment identified vulnerabilities of varying risk levels, including low, medium, and high severity issues. These findings highlight areas where security controls can be strengthened to reduce the risk of unauthorized access, data leakage, service disruption, or other security incidents. No testing activities caused disruption to business operations, and all testing was performed within the defined scope and rules of engagement. Based on the findings, remediation recommendations were provided to address the identified vulnerabilities and improve the overall security posture. Implementing these recommendations will help enhance system resilience, reduce attack surfaces,
and align security practices with industry best practices and compliance requirements.
Conclusion:
The Vulnerability Assessment and Penetration Testing (VAPT) exercise was successfully completed to evaluate the security posture of the assessed systems, applications, and network infrastructure within the defined scope. The assessment aimed to identify potential security weaknesses and validate their exploitability under real-world attack scenarios. The testing revealed a range of vulnerabilities with varying levels of severity, including low, medium, and high-risk findings. While no
critical system compromise was observed during the engagement, certain vulnerabilities pose a potential risk if left unaddressed. These weaknesses could be exploited to gain unauthorized access, compromise sensitive data, or disrupt business operations.
Remediation recommendations have been provided for each identified vulnerability. It is strongly advised that high and medium-risk issues be prioritized and addressed promptly, followed by lowrisk findings as part of ongoing security hygiene. A re-assessment is recommended after remediation to validate the effectiveness of corrective actions. In conclusion, this VAPT engagement has provided valuable insight into the current security posture and serves as a proactive step toward enhancing the organization’s cybersecurity resilience. Continuous security testing, combined with security
awareness and best practices, will help maintain a robust and secure environment against evolving
threats.

